Cyber security hazard in UDP – using solutions based on UDP or TCP?

A new kind of cyber security hazard was uncovered in UDP based solutions. POINTR is a TCP based solution, so POINTR users are not at risk. Find out whether your company is in danger.
Remote Collaboration Tools have become indispensable in many industries for a good reason, but many UDP based solutions are now vulnerable. POINTR is not effected by this new class of attacks as it is based on TCP only. If your company uses other remote collaboration solutions and/or video conferencing programs, you could be under attack right now.
All services based on the User Datagram Protocol (UDP) could be affected. These are in particular videoconferencing and web-meeting solutions. But also numerous remote collaboration solutions for industrial use are based on UDP. The cyber security hazard found by the data protection and security expert Samy Kamkar was presented here and elsewhere over the internet on November 2nd.
The XRTC protocol, which is developed by Delta Cygni Labs based on the Transmission Control Protocol (TCP) and is used in the remote collaboration tool POINTR, cannot be attacked in this way.
The attack point in the NAT Slipstreaming vulnerability is the inbound connection inherent for the UDP protocol. That makes it necessary to open your own firewall with a so-called pinhole port when computers in your own network communicate with computers outside your network. And this is the case for all video conferences with partners and customers or with employees whose computers are not in the company network. This is the case when Employees are working from home office or in the field for example.
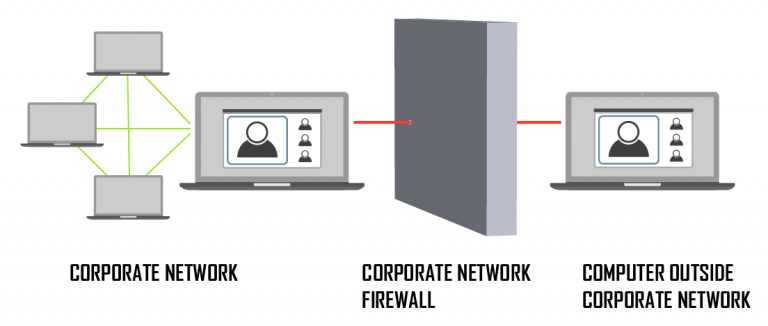
Remote collaboration solutions based on UDP also have to open this gateway. Now a method to enter through this pinhole is discovered to allow full access to the corporate network behind the firewall.
What makes POINTR so secure?
POINTR uses the proprietary XRTC protocol (Extended Realtime Communication) and is not only protected against the common online communication vulnerabilities by its architecture, but, since it does not use any inbound connections, it is also secured against the NAT Sliptstreaming attacks and other cyber security hazard types that could use the pinhole port entering method in the future.
The secure-by-design principle as foundation of XRTC
The development of XRTC protocol followed the Security by Design (SBD) approach. This means that the POINTR software’s protocol – unlike UDP, whose roots lie in online gaming – was designed from the ground up to be secure.
XRTC exclusively uses outgoing TLS1.2 connections and thus imitates the principle of Poste restante. All data packets are stored outside the own network in contrast to UDP. The data packets are not delivered straight “home” to the own address, but XRTC regularly collects the data packets from a letterbox located outside the firewall. In this way, XRTC does not allow any external supplier to enter, but also does not disclose its address to anyone it’s communicating with.
Want to read more about the most secure video call protocol? Find more about the unique XRTC protocol here!